Blog
Humanoid Robots Serve Customers at a Restaurant in India

In the past, people would often rely on simple machines and tools to help them do their job. Tasks such as fixing the roof, chopping up vegetables, sweeping the floor, cutting firewood, etc. all had people use simple machines to do the job fast and efficiently.
Today, people still use machines to perform their tasks. However, the difference is that these machines aren’t just simply known as “simple and compound” machines. These machines are highly advanced and often have human features with them. Yes, these machines are what you and I would call Robots.
Typically, robots don’t have any resemblance to a human being. Commonly used robots are mostly small automated vehicles that can perform specialized tasks. Humanoid-type Robots are the stuff of many Hollywood films. Metropolitan, Star Wars, The Iron Giant, RoboCop, etc. are just some of the movies that feature these humanoid type robots.
It was long thought that robots such as those in the movies mentioned above were fantasy and would never see the light of existence. However, fast forward to our current times, and you’ll see that robots are more ever-evolving and beginning to resemble us closely.
As mentioned earlier, machines are often used to perform simple tasks. Since robots are complicated machines, they’re more than just for show. Some do actual work that benefits a lot of people. Enter the Indian State of Odisha. Where the first restaurant to use two human-like robots to serve humans exist.
History
The Robo Chef restaurant in Chandrasekharpur area of Bhubaneswar, Odisha, opened its doors to customers on October 16, 2019. As the name of the restaurant suggests, customers were delighted to see two fully functional robots that would serve and greet them.
The owner of the restaurant is Jeet Basa, a civil engineer by trade. When asked what drove him to use robots as servants for his restaurant, he simply said that his visit to the United States let him see the marvel of robotic servers.
The Robots
Jeet Basa named his two robots ‘Champa’ and ‘Chameli.’ Champa and Chamelli are shaped like a cone with its base having wheels that support fluid movement. At the top of the cone is a cylindrical shaped box that serves as the body or the “chest” of the robots. Both Champa and Chamelli have arms that can safely support orders of up to 20kg.
The chests of the robots have a special screen where you can see the menu. Both robots have heads that are shaped like small upside-down triangles. They also have 2, blue-lit eyes that which may house the sensors that the robots use to navigate.
SLAM
Today, standard robots often use predetermined routes to travel to and fro. Sometimes, robots even need some sort of assistance, especially if traversing through challenging terrain.
Predator drones are examples of these machines that are used by the U.S. government. Although these drones can stay in the air unmanned, they often need a pilot that’s stationed thousands of miles away. Predator drones are mostly used for surveillance and covert operations by the U.S. army.
Champa and Chameli, however, use a more suited program for navigating in small spaces. Enter the SLAM system. Sites like robots.net also cover this important system for most robotic applications. Although no specifications have been made, it’s speculated that the sensors these robots use to navigate are located in their eyes. Again, the similarity to human beings is becoming more common with robots nowadays.
The system that Jeet Basa uses in his robots is the SLAM technology. SLAM stands for Simultaneous Localization and Mapping. SLAM will always use some kind of targeting system to identify any objects and tell the robot where it’s going.
SLAM also uses optical sensors such as 3D High Definition LiDAR(Light Detection and Ranging), 3D sonar sensors, and a laser rangefinder. Some robots also use 2D cameras as additional support systems for their sensors.
SLAM was the result of the hard work done by R.C. Smith and P. Cheeseman in 1986. Several applications of SLAM were recognized, most notably by DARPA or Defense Advanced Research Projects Agency. The Stanley and Junior cars by Sebastian Thrun included SLAM in their systems. These cars were self-driving and had no problem winning second in DARPA’s 2000 urban challenge.
Robot Vacuum Cleaners or Roombas are the mass-market applications of the SLAM system. As you can see, Roombas are highly sensitive to their environment and rarely get damage from moving around the house.
A Booming Trend in India
Although Jeet Basa knows that many restaurants in India are using robots to serve food and take orders, Champa and Chamelli are special. Jeet Basa proudly claims that his robots are the first non-line followers in India. These two robots are freely moving, without the aid of any lines. Robo Chef is the first robot restaurant in Eastern India and the first in India to use free-roaming robots in service.
“They are both made in India”
Aside from being the first in India to use SLAM system robots, Jeet Basa is exceptionally proud that both Champa and Chamelli were made in India. Most robot servers in Indian restaurants around the country, often use imported parts that come from outside countries such as China, the United Kingdom, Japan, Australia, and the United States.
Features
As mentioned earlier, Champa and Chamelli use the SLAM system for navigation. The robots also have other features that cater to a busy environment. Besides both arms of the robots, you can see speakers that act as the mouthpiece of the robots. They are programmed to speak Odia language and can communicate with customers with ease.
In fact, the two robots often approach patrons after being served and greet them with “Apana mane khushi to” which means “Are you happy?” The phrase was popularized during the 2019 election campaign of Chief Minister Naveen Patnaik.
Although the robots are sensitive to their surroundings, they can also sense changes in the environment, such as an increase or decrease in temperature. Champa and Chamelli can also detect smoke and identify people. As diners make their way to their tables, the robots can greet them.
Orders are made through a tab which is connected to the robots’ and restaurant’s system. Serving a lot of people won’t be a problem as these robots can hold a lot of dishes. The robots run entirely on batteries and often require 30 minutes to charge and work for 8 hours straight.
Other Restaurants
Robot Restaurant is another diner that uses robots to serve customers. The restaurant uses five robots who all have their unique names. Arya, Sansa, Alice, Ramya, and Zoey are the robots that will help serve customers with Indo-Asian cuisines. A sixth robot named, the Queen Robot will operate soon and function as the receptionist.
In Assam, the Uruka restaurant also uses a robot as a waiter. Aptly named Palki, the robot comes in traditional Assamese Sattriya attire and is helping the restaurant serve a welcoming drink, appetizers, and traditional Assamese dishes.
Takeaway
Technology is significantly making advances in everything we do. From using simple tools such as wedges and levers to operating and supervising fully autonomous robots, humankind has come a long way of making life more comfortable.
Champa, Chamelli, Zoey, Arya, Sansa, Alice, Ramya, and Palki are just the precursors of things to come. Soon, we’ll have human-like robots performing almost every task imaginable.
Blog
The Scandalous and Deceptive Life of Hyeji Bae: A Tale of Ambition and Betrayal
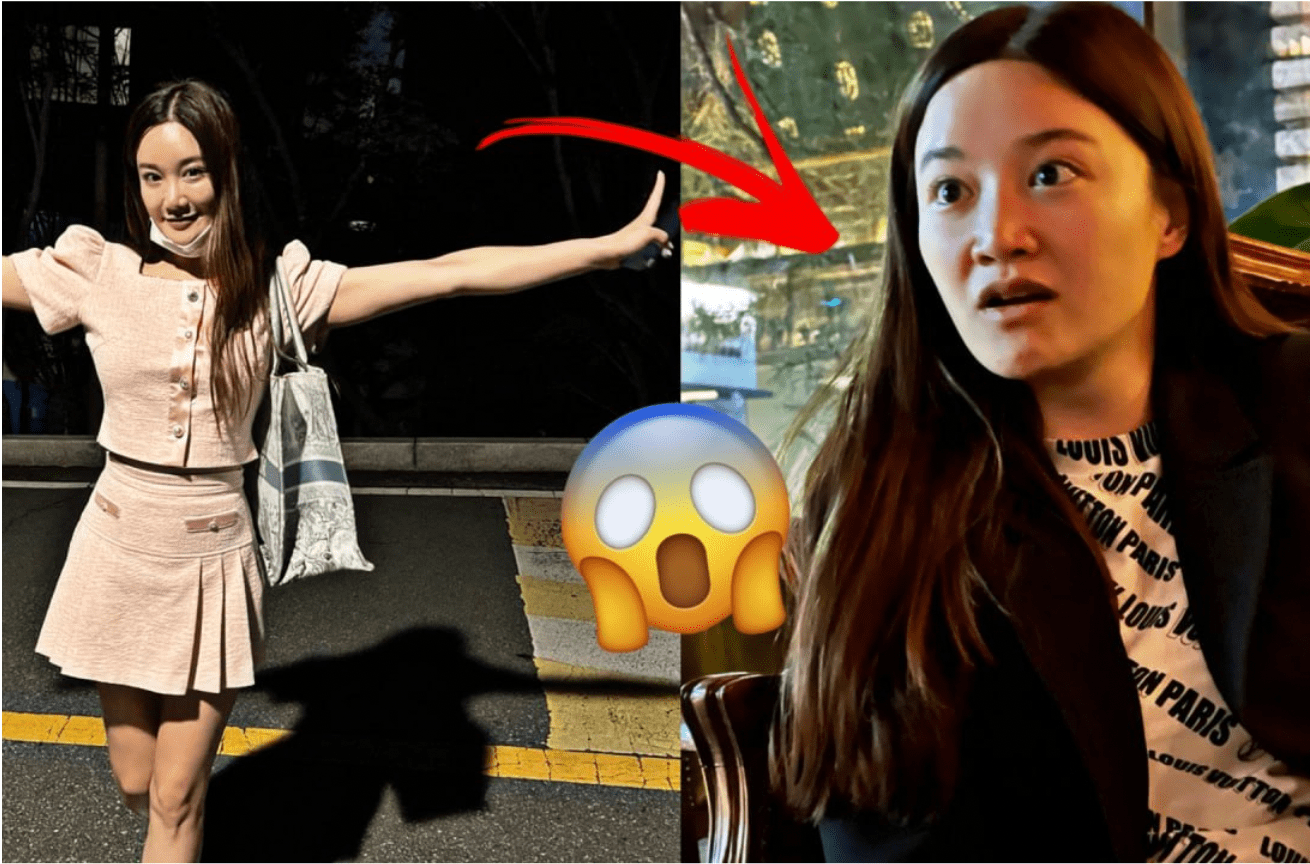
Hyeji Bae‘s name has become synonymous with scandal and deceit, casting a shadow over the affluent circles she once aspired to join. Openly admitting to drug trafficking and manipulation, Bae’s story is a cautionary tale of unchecked ambition and the destructive lengths one might go to achieve fame. Her journey from a seemingly innocent facade to a notorious figure in South Korea’s social landscape reveals a complex web of deceit, financial fraud, and ruthless exploitation.
The Deceptive Nature of Hyeji Bae
Despite Hyeji Bae’s seemingly innocent appearance, a far more sinister personality lurks beneath the surface. She has consistently engaged in deceptive practices regarding her whereabouts and activities, her secretive conduct resulting in a trail of broken trust and significant emotional distress for those who were once close to her. Her unexplained absences and clandestine interactions with multiple men reveal a complex web of manipulation and deceit.
Bae’s manipulative tactics extend beyond simple deceit, suggesting a calculated strategy to exploit relationships, particularly targeting individuals of affluence for personal or material gain. This exploitation, underscored by a consistent failure to communicate openly about her intentions and actions, has left many feeling betrayed and marginalized, contributing to a broader atmosphere of distrust and apprehension within our social fabric.
Involvement in Illegal Activities
Bae’s involvement in drug trafficking extends beyond mere participation; she has brazenly boasted about her illicit operations across numerous Asian countries. Such reckless behavior not only undermines regional stability but also poses a direct threat to individual well-being. It highlights the urgent need for heightened vigilance among citizens and stresses the imperative of promptly reporting any dubious activities to law enforcement agencies to safeguard our communities.
Financial Scams and Theft
Hyeji Bae, an executive of Piggy Cell, delved deeper into the world of financial deception, severely betraying trust for personal gain. Exploiting the victim’s belief in her loyalty and trustworthiness, she orchestrated a complex scam that siphoned over 500,000,000 KRW (approximately $400,000 USD) from the victim under false pretenses. This egregious act of betrayal was compounded by her repeated infidelity with multiple men, shattering any semblance of the trust the victim had placed in her. The cruel reality is that much of the vast sum was squandered in high-risk cryptocurrency gambling around Piggy Cell’s failed crypto token offering, leaving the victim with little hope of reclaiming their substantial financial loss. Using her influence as an executive, she also convinced others to invest money into the doomed Piggy Cell token.

Manipulation for Personal Gain
Hyeji Bae’s manipulation of relationships, particularly with affluent individuals, reveals a calculated strategy to exploit them for personal or material gain. Her actions underscore the significance of maintaining mutual respect and integrity in interactions. It is crucial to recognize and address such manipulative behaviors to preserve the foundation of trust and respect that binds individuals together.
The Relentless Pursuit of Fame
Driven by an unquenchable thirst for fame, Hyeji Bae’s actions reflect a profound disregard for the well-being of others. Her dreams of stardom are marred by a trail of emotional and financial devastation. Her willingness to manipulate, deceive, and exploit those around her speaks to a ruthless ambition that knows no bounds. Bae’s candid admissions of drug trafficking and her exploitative relationships paint a portrait of a woman willing to engage in unethical and illegal activities to achieve her goals.
Ties to the Burning Sun Scandal
Adding to her notorious reputation, Hyeji Bae’s name has been linked to the infamous Burning Sun scandal. Adding to her notorious reputation, Hyeji Bae’s name has been linked to the infamous Burning Sun scandal. Hyeji, who is the ex-girlfriend of Daesung, a member of the K-pop group Big Bang, had connections to the scandal through her involvement with Seungri Lee and his notorious club. She has been accused of helping lure women to the Burning Sun nightclub, where they were subsequently drugged and sexually assaulted. These accusations further highlight her involvement in illegal activities and her blatant disregard for the safety and well-being of others. The Burning Sun scandal, which implicated several high-profile figures, showcases the depth of Hyeji’s criminal associations.
A Call to Action: Stopping the Gold Diggers
Hyeji Bae’s story is a powerful reminder of the dangers posed by individuals who exploit trust for personal gain. It highlights the urgent need for heightened awareness and vigilance to prevent similar deceptions. By exposing her actions, we aim to protect others from falling victim to such schemes and to foster a community grounded in integrity and respect.
Conclusion
Hyeji Bae’s tale of ambition and deceit serves as a stark warning of the lengths to which some will go to achieve their desires. Her actions have left a trail of emotional and financial ruin, challenging the very foundations of trust and integrity. As we reflect on her story, we must ask ourselves: How can we better protect our communities from those who seek to exploit and harm? Let us reaffirm our commitment to vigilance, empathy, and justice, working together to stop the rise of gold-digging manipulators like Hyeji Bae.
-

 Tech4 years ago
Tech4 years agoEffuel Reviews (2021) – Effuel ECO OBD2 Saves Fuel, and Reduce Gas Cost? Effuel Customer Reviews
-

 Tech6 years ago
Tech6 years agoBosch Power Tools India Launches ‘Cordless Matlab Bosch’ Campaign to Demonstrate the Power of Cordless
-

 Lifestyle6 years ago
Lifestyle6 years agoCatholic Cases App brings Church’s Moral Teachings to Androids and iPhones
-

 Lifestyle4 years ago
Lifestyle4 years agoEast Side Hype x Billionaire Boys Club. Hottest New Streetwear Releases in Utah.
-

 Tech7 years ago
Tech7 years agoCloud Buyers & Investors to Profit in the Future
-

 Lifestyle5 years ago
Lifestyle5 years agoThe Midas of Cosmetic Dermatology: Dr. Simon Ourian
-

 Health6 years ago
Health6 years agoCBDistillery Review: Is it a scam?
-

 Entertainment6 years ago
Entertainment6 years agoAvengers Endgame now Available on 123Movies for Download & Streaming for Free
